Researchers Find Android Phones Still Track You, Even When You Opt Out
If you use an Android cellular phone and are (rightfully!) concerned about electronic privacy, you have almost certainly taken treatment of the fundamental principles now. You have deleted the snoopiest of the snoopy applications, opted out of monitoring every time doable, and taken all of the other precautions the common how-to privacy guides have told you to. The lousy news—and you could want to sit down for this—is that none of individuals ways are plenty of to be fully free of charge of trackers.
Or at minimum, that’s the thrust of a new paper from researchers at Trinity School in Dublin who took a look at the info-sharing habits of some common variants of Android’s OS, including individuals formulated by Samsung, Xiaomi, and Huawei. According to the researchers, “with minimal configuration” proper out of the box and when left sitting idle, these equipment would incessantly ping again gadget info to the OS’s developers and a slew of picked 3rd parties. And what is worse is that there’s generally no way to decide out of this info-pinging, even if people want to.
A great deal of the blame listed here, as the researchers place out, drop on so-referred to as “system applications.” These are applications that come pre-put in by the hardware maker on a sure gadget in purchase to offer a sure sort of features: a camera or messages app are examples. Android frequently deals these applications into what is known as the device’s “read only memory” (ROM), which means you just can’t delete or modify these applications without the need of, effectively, rooting your gadget. And right until you do, the researchers identified they were being continuously sending gadget info again to their dad or mum company and additional than a handful of 3rd parties—even if you never opened the app at all.
Here’s an illustration: Let’s say you own a Samsung gadget that comes about to be packaged with some Microsoft bloatware pre-put in, including (ugh) LinkedIn. Even though there’s a fantastic probability you’ll never open LinkedIn for any motive, that challenging-coded app is continuously pinging again to Microsoft’s servers with information about your gadget. In this situation, it is so-referred to as “telemetry info,” which consists of information like your device’s exclusive identifier, and the amount of Microsoft applications you have put in on your cellular phone. This info also gets shared with any 3rd-celebration analytics suppliers these applications could have plugged in, which typically means Google, considering the fact that Google Analytics is the reigning king of all the analytics equipment out there.
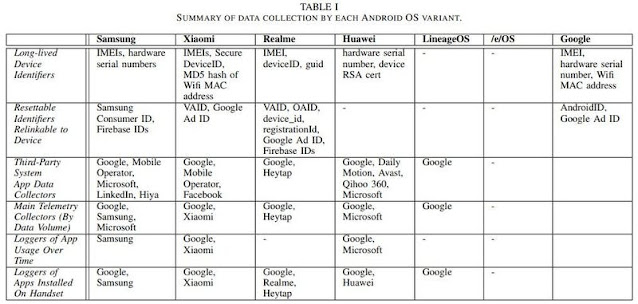
As for the challenging-coded applications that you could really open each and every after in a even though, even additional info gets despatched with each and every conversation. The researchers caught Samsung Pass, for illustration, sharing information like timestamps detailing when you were being using the app, and for how prolonged, with Google Analytics. Ditto for Samsung’s Activity Launcher, and each and every time you pull up Samsung’s virtual assistant, Bixby.
Samsung is not on your own listed here, of program. The Google messaging app that comes pre-put in on phones from Samsung competitor Xiaomi was caught sharing timestamps from each and every consumer conversation with Google Analytics, along with logs of each and every time that consumer despatched a textual content. Huawei equipment were being caught executing the exact same. And on equipment where by Microsoft’s SwiftKey arrived pre-put in, logs detailing each and every time the keyboard was used in an additional app or elsewhere on the gadget were being shared with Microsoft, as a substitute.
We have barely scratched the surface listed here when it comes to what each and every app is executing on each and every gadget these researchers appeared into, which is why you should look at out the paper or, greater nonetheless, look at out our handy manual on spying on Android’s info-sharing practices by yourself. But for the most aspect, you’re going to see info becoming shared that appears to be like quite, effectively, monotonous: event logs, information about your device’s hardware (like model and display dimensions), along with some sort of identifier, like a phone’s hardware serial amount and mobile ad identifier, or “AdID.”
On their own, none of these info details can establish your cellular phone as uniquely yours, but taken jointly, they variety a exclusive “fingerprint” that can be used to track your gadget, even if you check out to decide out. The researchers place out that even though Android’s advertising ID is technically resettable, the reality that applications are commonly receiving it bundled with additional everlasting identifiers means that these apps—and whatever 3rd parties they are doing work with—will know who you are in any case. The researchers identified this was the situation with some of the other resettable IDs supplied by Samsung, Xiaomi, Realme, and Huawei.
To its credit score, Google does have a handful of developer policies intended to hinder significantly invasive applications. It tells devs that they just can’t hook up a device’s exclusive ad ID with some thing additional persistent (like that device’s IMEI, for illustration) for any sort of ad-associated reason. And even though analytics suppliers are permitted to do that linking, they can only do it with a user’s “explicit consent.”
“If reset, a new advertising identifier ought to not be related to a previous advertising identifier or info derived from a previous advertising identifier without the need of the explicit consent of the consumer,” Google explains on a separate web site detailing these dev guidelines. “You ought to abide by a user’s ‘Opt out of Interest-dependent Advertising’ or ‘Opt out of Adverts Personalization’ location. If a consumer has enabled this location, you may well not use the advertising identifier for producing consumer profiles for advertising applications or for concentrating on people with personalized advertising.”
It’s really worth pointing out that Google places no policies on no matter if developers can accumulate this data, just what they are permitted to do with it immediately after it is collected. And since these are pre-put in applications that are generally caught on your cellular phone, the researchers identified that they were being generally permitted to facet-phase user’s privacy explicit decide-out settings by just… chugging along in the track record, regardless of no matter if or not that consumer opened them. And with no straightforward way to delete them, that info collection’s going to hold on going on (and hold on going on) right until that phone’s proprietor possibly gets artistic with rooting or throws their gadget into the ocean.
Google, when requested about this un-decide-out-ready info assortment by the individuals more than at BleepingComputer, responded that this is basically “how modern day smartphones work”:
As explained in our Google Engage in Products and services Aid Center write-up, this info is critical for core gadget providers this sort of as force notifications and software updates across a assorted ecosystem of equipment and software builds. For illustration, Google Engage in providers makes use of info on qualified Android equipment to assist core gadget options. Collection of minimal standard data, this sort of as a device’s IMEI, is important to supply essential updates reliably across Android equipment and applications.
Which sounds reasonable and fair, but the review alone proves that it is not the complete tale. As aspect of the review, the workforce appeared into a gadget outfitted with /e/OS, a privacy-centered open-source working procedure that’s been pitched as a “deGoogled” variation of Android. This procedure swaps Android’s baked-in apps—including the Google Engage in store—with free of charge and open source equivalents that people can access with no Google account needed. And wouldn’t you know it, when these equipment were being left idle, they despatched “no data to Google or other 3rd parties,” and “essentially no information” to /e/’s devs them selves.
In other text, this aforementioned monitoring hellscape is plainly only inescapable if you sense like Google’s presence on your phones is inescapable, way too. Let’s be sincere here—it sort of is for most Android people. So what is a Samsung consumer to do, moreover, y’know, get tracked?
Effectively, you can get lawmakers to treatment, for starters. The privacy guidelines we have on the publications today—like GDPR in the EU, and the CCPA in the U.S.—are practically solely created to handle the way tech businesses tackle identifiable forms of info, like your title and handle. So-referred to as “anonymous” info, like your device’s hardware specs or ad ID, typically falls via the cracks in these guidelines, even though they can typically be used to establish you regardless. And if we just can’t effectively demand an overhaul of our country’s privacy guidelines, then perhaps a person of the a lot of significant antitrust fits Google’s staring down proper now will at some point get the company to put a cap in some of these invasive practices.








