Privileged access management a must in 2020
Dependent on current danger activity, privileged accounts, not company data, may be the most important products in just company networks.
Quite a few sessions at Gartner’s 2020 Safety & Threat Management Summit this 7 days targeted on the great importance of privileged access management to cybersecurity, and how danger actors have more and more targeted initiatives to hijack or acquire privileged accounts. In a Monday session titled “Outlook for Id and Access Management,” Gartner senior analysis director David Mahdi mentioned what a thriving identity and access management (IAM) plan looks like in 2020, as well as the expanding great importance of privileged access management and other matters.
Mahdi’s presentation mentioned the idea of speed versus accuracy in a crisis circumstance when promptly responding to a crisis, speed of response to “end the bleeding” is far more crucial than accuracy at the second. When the crisis moves from “reply” to “recuperate” and “renew,” then it is crucial to commence pondering about how a organization can get back again up on its toes and how it can build a far more efficient cybersecurity foundation for the potential.
Fantastic IAM, Mahdi mentioned, is like a fantastic pit crew that balances the great importance of obtaining a racer back again on the keep track of swiftly (speed) with the great importance of producing absolutely sure a wheel does not arrive off mid-race (accuracy). To give an organization “speed for survival,” Mahdi encouraged prioritizing the enablement of safe remote access, federated SSO and multifactor authentication (MFA) and each quickly and “fantastic adequate” IAM and purchaser IAM or CIAM. And then to maintain accuracy, an organization should really target on account takeover security, fraud detection, privileged access management and converged, much less expensive SaaS-sent IAM.
“If you aren’t applying privileged access management equipment, technological know-how, people and approach in which you have this embedded in the fabric of your organization, now’s the time to do it. Why? Lousy fellas are going right after privileged customers. Privileged customers have access to your sensitive data, and they have access to the keys to your kingdom. And which is what you really want to protect,” Mahdi mentioned.
In another Monday presentation that touched on privileged access management, titled “Deconstructing the Twitter Assault — The Job of Privileged Accounts,” CyberArk principal options engineer Matt Tarr mentioned the social engineering attack versus Twitter from this summertime that resulted in approximately $121,000 in bitcoin currently being ripped off from customers. He argued “fundamental person protection education” and privileged access management could have slowed or stopped the activities from unfolding.
“This attack highlights the dangers of unsecured privileged access. It should really remind us how swiftly any credential or identity can become privileged less than selected conditions. If not appropriately secured, external attackers and destructive insiders alike can use them to unlock critical belongings, irrespective of whether which is with a area admin or a basic aid account that can make adjustments with a Twitter profile,” he mentioned.
Tarr famous the notorious attack was not always innovative both.
“Initially assumed to be the get the job done of experienced country-state attackers, it now appears the social engineering-initiated attack was performed by a comparatively unsophisticated group of hackers enthusiastic by money obtain and/or interesting display names,” he mentioned. “Yup, display names.”
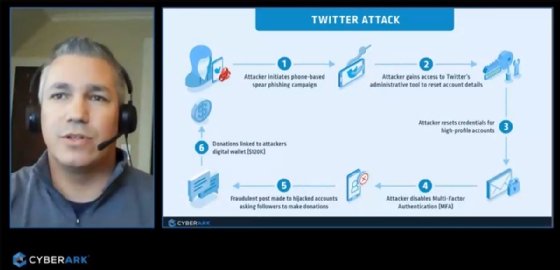
Tarr mentioned the breach shown that it was much easier for the attackers to split into Twitter by itself than to split into a Twitter account with MFA enabled. The attack started with a mobile phone-centered spear phishing or vishing campaign that qualified distinct Twitter workers. As soon as the attackers attained personnel credentials, they attained access to Twitter’s administrative equipment and disabled the MFA security on several large-profile accounts. Since Twitter lacked appropriate protection controls all around all those admin equipment, the attackers ended up ready to abuse them when remaining less than the radar. In essence, Twitter had improved account security for customers than it did for its possess directors, he mentioned.
Tarr mentioned mitigations versus these sorts of social engineering assaults that may happen in the potential. He encouraged cybersecurity consciousness education for workers, applying robust passwords, prioritizing privileged access management and building a conditional coverage that mandates multifactor authentication.
In a Tuesday session, titled “Safety Leader’s Manual to Privileged Access Management,” Gartner analysis director Felix Gaehtgens mentioned privileged access management is a important element of any protection plan simply because of the more and more substantial scope of IT environments, privileged customers, administrative equipment, and IAM data these kinds of as passwords, encryption keys and certificates. Gaehtgens encouraged corporations put into practice stringent controls on privileged access these kinds of as limiting the whole number of personal privileged accounts, building far more shared accounts and cutting down the situations and durations for the duration of which privileged access is granted.








