New ‘Thanos’ ransomware weaponizes RIPlace evasion technique
Danger researchers at Recorded Long term identified a new ransomware-as-a-assistance device, dubbed “Thanos,” that is the initial to employ the evasion approach recognized as RIPlace.
Thanos was put on sale as a RaaS device “with the potential to deliver new Thanos ransomware shoppers based mostly on 43 different configuration possibilities,” in accordance to the report printed Wednesday by Recorded Future’s Insikt Team.
Notably, Thanos is the initial ransomware spouse and children to publicize its optional utilization of RIPlace, a approach released by way of a evidence-of-thought (PoC) exploit in November 2019 by safety corporation Nyotron. At its release, RIPlace bypassed most existing ransomware defense mechanisms, which includes antivirus and EDR items. But despite this, the evasion wasn’t thought of a vulnerability due to the fact it “experienced not basically been observed in ransomware at the time of crafting,” Recorded Future’s report said.
As documented by BleepingComputer very last November, only Kaspersky Lab and Carbon Black modified their software to protect towards the approach. But considering the fact that January, Recorded Long term said, “Insikt Team has observed associates of dim web and underground discussion boards utilizing the RIPlace approach.”
According to its report on RIPlace, Nyotron identified that file substitute steps utilizing the Rename functionality in Windows could be abused by contacting DefineDosDevice, which is a legacy functionality that results in a symbolic connection or “symlink.”
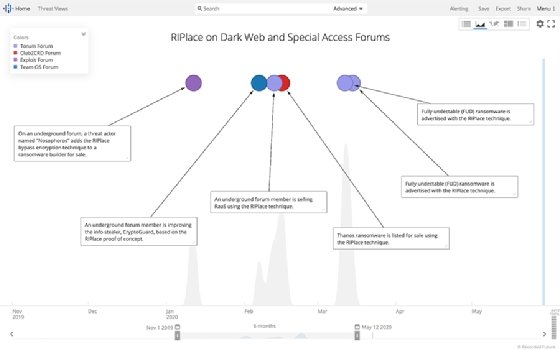
Lindsay Kaye, director of operational outcomes for Recorded Future’s Insikt Team, instructed SearchSecurity that threat actors can use the MS-DOS machine title to substitute an primary file with an encrypted edition of that file without having altering most antivirus plans.
“As component of the file rename, it named a functionality that is component of the Windows API that results in a symlink from the file to an arbitrary machine. When the rename call then comes about, the callback utilizing this handed-in machine path returns an error nevertheless, the rename of the file succeeds,” Kaye said. “But if the AV detection doesn’t handle the callback appropriately, it would miss ransomware utilizing this approach.”
Insikt Team researchers initial identified the new Thanos ransomware spouse and children in January on an exploit forum. According to the Recorded Long term report, Thanos was developed by a threat actor recognized as “Nosophoros” and has code and functions that are very similar to a further ransomware variant recognized as Hakbit.
When Nyotron’s PoC was ultimately weaponized by the Thanos threat actors, Kaye was in favor of the vendor’s determination to publicly release RIPlace very last year.
“I assume at the time, publicizing it was excellent in that now antivirus providers can say excellent, now let us make absolutely sure it truly is some thing we are detecting due to the fact if someone’s declaring here is a new approach, threat actors are likely to take edge of it so now it truly is some thing that is not likely to be discovered out just after men and women are victimized. It really is out in the open up and providers can be conscious of it,” Kaye said.
Recorded Future’s report mentioned that Thanos appears to have received traction within the threat actor community and will continue on to be deployed and weaponized by both of those personal cybercriminals and collectives by way of its RaaS affiliate method.






