Microsoft Discovered New ‘Powerdir’ macOS Vulnerability, Fixed in 12.1 Update
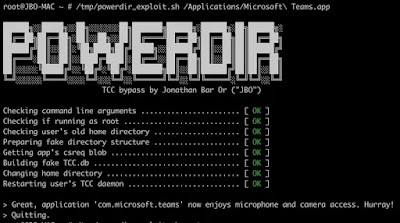
This morning, Microsoft’s 365 Defender investigate team introduced details of a new macOS “Powerdir” vulnerability that permits an attacker to bypass transparency, consent, and control technology to obtain unauthorized accessibility to secured facts.
Apple has now preset vulnerability CVE-2021-30970 in the macOS Monterey 12.one Update introduced in December, so people who have upgraded to the latest model of Monterey are secured. Those who haven’t should really update. Apple in its Protection Launch Notes for Update 12.1 confirmed the vulnerability of TCC and attributed its discovery to Microsoft.
In accordance to Microsoft, the “Powerdir” security vulnerability could permit the set up of a fake TCC database.
TCC is a very long-long lasting macOS aspect that permits people to configure the privateness configurations of their applications, and with the fake database, an attacker could hijack an application put in on a Mac or put in their individual malicious application by getting accessibility to the microphone and the camera to get hold of confidential facts.
Microsoft has a detailed description of how the vulnerability operates, and the business says its security researchers carry on to “observe the risk landscape” for new vulnerabilities and assault tactics influencing macOS and other non-Home windows units.
“Software package vendors like Apple, security researchers, and the larger security group, want to repeatedly function with each other to detect and fix vulnerabilities right before attackers can get advantage of them,” wrote Microsoft’s security team.







