Log4Shell: How to detect the Log4j vulnerability in your applications
Yesterday the Apache Basis released an unexpected emergency update for a vital zero-day vulnerability in Log4j, a ubiquitous logging tool included in pretty much each Java application. The situation has been named Log4Shell and gained the identifier CVE-2021-44228.
The trouble revolves all over a bug in the Log4j library that can allow an attacker to execute arbitrary code on a program that is working with Log4j to create out log messages. This security vulnerability has a broad effects and is some thing everyone with an application that contains Log4j desires to quickly spend attention to.
Why addressing Log4Shell is a major obstacle
Log4j is a library that is employed by lots of Java apps. It is one of the most pervasive Java libraries to date. Most Java apps log details, and there is nothing that tends to make this a lot easier than Log4j.
The obstacle listed here is discovering Log4j mainly because of the way Java packaging is effective. It is attainable you have Log4j hiding somewhere in your application and never even know it.
In the Java ecosystem, dependencies are distributed as Java archive (JAR) documents, which are packages that can be employed as a Java library. Typically employed tools, this kind of as Maven and Gradle, can routinely add JAR documents as you build your Java application. It is also attainable for a JAR to have another JAR to satisfy a dependency, which usually means a vulnerability can be concealed numerous concentrations down in your application. In some scenarios, one dependency pulls in hundreds of other dependencies building it even more hard to find.
Effectively, in the Java planet, you can have a JAR nested in a JAR nested in a JAR. This results in lots of layers that all have to have to be investigated. Just on the lookout at the JARs your task pulls in immediately may well not be ample, considering the fact that Log4j could be hiding inside of another JAR file!
Scan for Log4j with open up supply tools
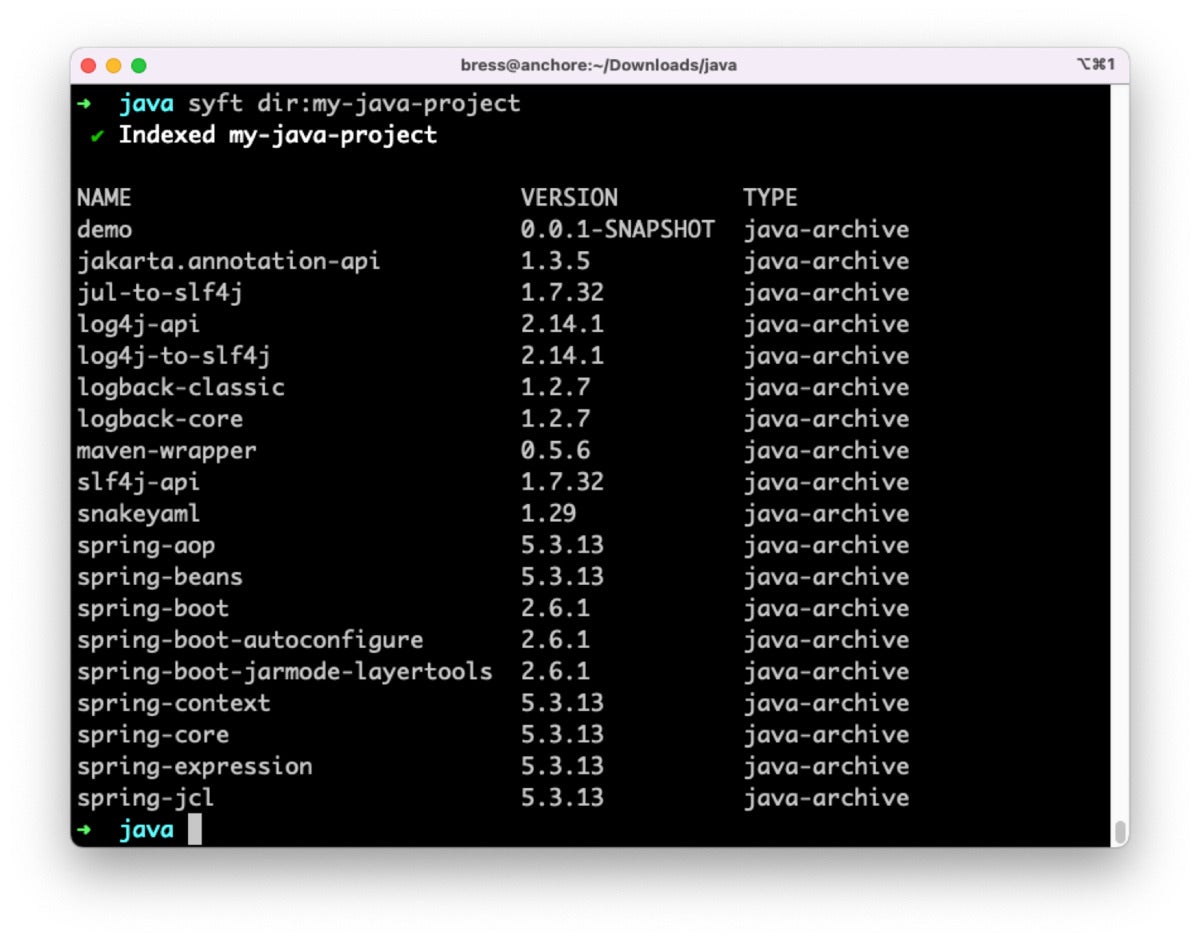
Syft is also in a position to discern which edition of Log4j a Java application incorporates. The Log4j JAR can be immediately included in our task, or it can be concealed away in one of the dependencies we contain. For example, working with Syft to scan this sample Java task displays that it features Log4j edition two.14.one, which is vulnerable to Log4Shell.
 Anchore
AnchoreIrrespective of the edition of Log4j that is included, there is worth in building and storing an SBOM to hold a record of every thing that is included in any program component or application you deliver. When a new vulnerability is identified, this kind of as Log4Shell, it’s significantly more rapidly to research as a result of a repository of SBOMs than it is to find and scan all of your Java apps.
Grype is a scanner that has the capacity to tell us which precise vulnerabilities our program incorporates. When you contain a dependency in your application you can also detect the vulnerabilities that the dependency incorporates, and so on as a result of multiple concentrations of nesting. Grype can scan the program immediately, or scan the SBOM produced by Syft. This enables you to re-scan the SBOM for new vulnerabilities even just after the program has been deployed or shipped to clients.
Scanning the exact sample Java task with Grype finds the Log4j vulnerability and identifies it as a vital severity.
 Anchore
AnchoreSyft and Grype have the capacity to scan your apps no make any difference exactly where they reside. You can scan a directory on disk, scan a container impression domestically, or even scan a container in a remote registry. You can scan supply code in advance of making, or the final application just after it’s built. It is essential to scan your apps all through each phase of advancement, just mainly because a supply code scan is thoroughly clean doesn’t imply the final build will be. Even scanning just after deployment is a good plan. Maybe you did not select up a vital Log4j vulnerability final week, but you may possibly this week!
Preserve Syft and Grype useful
Any time a new zero-day vulnerability is found out, it can be hard and demanding for impacted companies to remediate the trouble swiftly. The initially and most essential move is to recognize if a unique vulnerability even affects you, and in the case of JAR documents it can be a obstacle to recognize this with out tooling. Anchore’s open up supply Grype and Syft tools dig all the way to the bottom of your dependency tree to detect if there is a copy of Log4j hiding somewhere.
As an sector, how we react and support each individual other all through zero-day vulnerabilities is vital. Now is the time to share options and awareness to enable avoid breaches like this in the coming a long time.
Josh Bressers is VP of security at Anchore.
—
New Tech Forum gives a venue to explore and go over rising organization engineering in unparalleled depth and breadth. The selection is subjective, primarily based on our select of the systems we consider to be essential and of greatest curiosity to InfoWorld visitors. InfoWorld does not settle for marketing collateral for publication and reserves the appropriate to edit all contributed content material. Send all inquiries to [email protected].
This tale, “How to detect the Log4j vulnerability in your apps” was initially posted by
Macworld Insider.
Copyright © 2021 IDG Communications, Inc.







