Google unravels state-of-art Android and Windows exploit chains – Security
Google’s Project Zero security researchers have published a six-part detailed analysis of a set of vulnerabilities found on two exploit servers early last year that were to be used in so-called watering hole attacks with compromised web servers used to hack targets.
The report details the work of what Project Zero says is the work of “a highly sophisticated actor” who operates a complex targeting infrastructure.
Project Zero did not indicate who the actor might be, but said the exploit chains found are designed for efficiency and flexibility through their modularity.
“They are well-engineered, complex code with a variety of novel exploitation methods, mature logging, sophisticated and calculated post-exploitation techniques, and high volumes of anti-analysis and targeting checks,” the Project Zero researchers said.
“We believe that teams of experts have designed and developed these exploit chains.”
The researchers found exploits for four bugs in the Google Chrome web browser, one of which was a zero day when reported on February 18 last year.
Two zero-days exploiting font rendering vulnerabilities in Microsoft Windows were also discovered, along with a heap buffer overflow bug in the Client/Server Runtime Subsystem (CSRSS) that was abused to escape sandboxing or software execution restrictions in the operating system.
In contrast, the attackers used known exploits for Android devices.
The teams of highly skilled developers who built and assembled the exploit chains devised the attacks to have four stages.
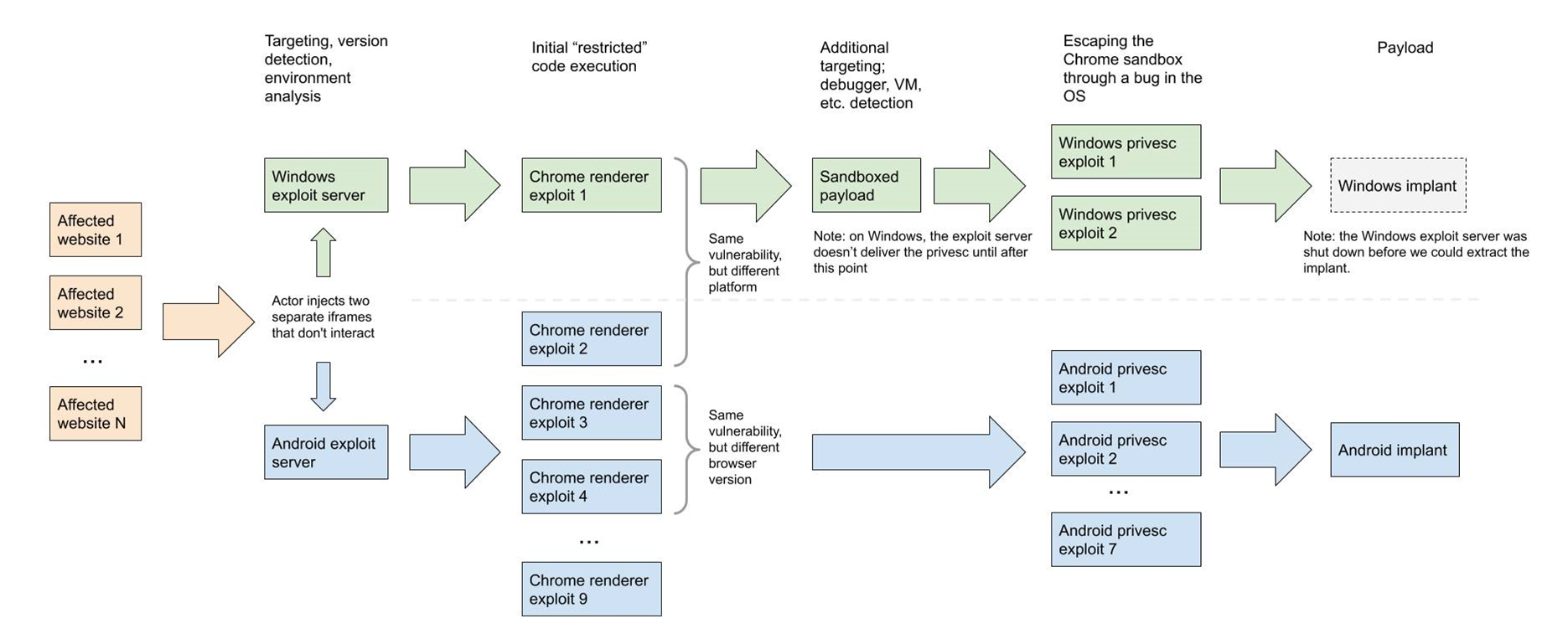
Detailed information on compromised devices was sent during stage 3 in the exploit chain to command and control servers for additional targeting beyond the first two stages.
The malicious code for stage 3 impressed the Project Zero researchers with its high quality.
“It’s especially fascinating how complex and well-engineered this stage 3 code is when you consider that the attackers used all publicly known n-days [known vulnerabilities] in stage 2,” the researchers said.
The attackers used a Google Chrome 0-day in stage 1, public exploit for Android n-days in stage 2, and a mature, complex, and thoroughly designed and engineered stage 3.
“This leads us to believe that the actor likely has more device-specific 0-day exploits.”
Stage 3 would also download the final payload for the attacks configured with the information sent to the control and command server, but Project Zero did not provide details on what the Android implant they had captured does.
The threat actors shut down their Windows attack server before Project Zero was able to extract the implant from there.
Asked why Project Zero released the detailed analysis of the exploit chain almost a year after the malware was found, security researcher Maddie Stone cited delays brought on by the Covid-19 pandemic, and having four co-authors including herself.
“We definitely want to get things out sooner in the future,” Stone told iTnews.
Team lead for Project Zero Tim Willis pointed out that the research published today does not cover the in-the-wild vulnerabilities found in October 2020.
That investigative work is still ongoing and will take a few more months.







