Dell BIOSConnect flaws affect 30 million devices
Security vendor Eclypsium has found out four vulnerabilities that affect 128 Dell product types, and an estimated thirty million person units, that permit danger actors to remotely execute code in a pre-boot natural environment, according to new research unveiled Thursday.
The report, titled “BIOS Disconnect,” facilities on vulnerabilities involving Dell’s BIOSConnect tool in SupportAssist. SupportAssist is a standard guidance tool that comes preinstalled on most Dell Windows computers and tablets, and BIOSConnect is a tool inside it employed for firmware updates and distant working process recovery.
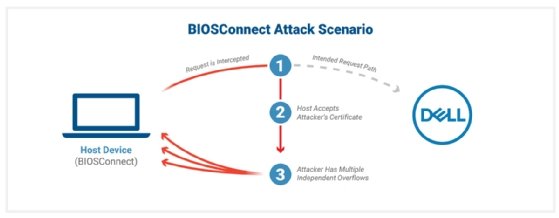
The main vulnerability requires an insecure TLS link among Dell and the BIOS. The report clarifies that the BIOSConnect TLS link will settle for “any valid wildcard certificate.”
“When making an attempt to hook up to the backend Dell HTTP server, the TLS link from BIOSConnect will settle for any valid wildcard certificate. This will allow an attacker with a privileged community place to impersonate Dell and deliver attacker-managed written content again to the target product,” the report reads.
Eclypsium principal researcher Jesse Michael explained to us the certificate Eclypsium effectively employed in the assault circumstance charge the organization all around 70 or 80 Euros.
The other three vulnerabilities are overflow vulnerabilities enabled by the insecure TLS link being exploited and permit arbitrary code execution at the BIOS/Unified Extensible Firmware Interface (UEFI) level. That claimed, as Scott Scheferman, Eclypsium’s principal cyber strategist, described, there are scenarios the place these added vulnerabilities usually are not necessary to execute destructive code on a target process.
“If you have Protected Boot disabled, for case in point, you never need to have the three buffer overflows,” Scheferman claimed.
“All three vulnerabilities are independent, and every one particular could direct to arbitrary code execution in BIOS,” the report claimed.
The vulnerability CVEs are CVE-2021-21571, CVE-2021-21572, CVE-2021-21573 and CVE-2021-21574. Michael claimed all four vulnerabilities can be exploited remotely. The vulnerability chain, according to the report, has a cumulative Common Vulnerability Scoring Process score of 8.three, which is viewed as “superior” in phrases of severity.
The 128 Dell types impacted include private and business desktops, laptops and tablets. This contains, as the report claimed, “units protected by Protected Boot and Dell Secured-main PCs.” Michael claimed that when the class of vulnerability is frequent, these unique vulnerabilities were special to Dell.
Requested about what shocked him most about the vulnerabilities, Scheferman pointed to Dell being at the centre of it.
“Absorbing it for the very first time, the very first matter that went as a result of my brain was, how does a key OEM get TLS improper the place it issues most to the device’s have faith in?” he claimed. “How did you get it improper in the yr 2021 when TLS has been overwhelmed up on for thirty many years?”
Though Eclypsium has observed no danger action associated to the Dell BIOSConnect vulnerabilities to date, together with both exploitation and scanning, Scheferman claimed exploitation could have sizeable penalties.
“The affect of this vulnerability, were it to be exploited in the wild as component of a marketing campaign, could be remarkable since you get persistence at the UEFI, and all the protection controls on the working process — AV, EDR, SIEM, SOAR, XDR, all that things — none of that would at any time see this happen since that working process is off. It is really happening at the UEFI. You have omnipotence and a type of indefinite persistence if you acquire entry there,” he claimed.
Michael claimed the vulnerabilities were very first found out in March. Right after informing Dell, Michael claimed Eclypsium gave them the business-standard ninety-day disclosure timeline, moreover an added two months.
However, as this report goes dwell, not every problem will be mounted.
“[Dell is] having some troubles finding some of the fixes out, so they are finding some fixes out now and will be pushing extra fixes out and, I believe, have everything out by the stop of July,” Michael claimed.
According to the report, Dell claimed “a the greater part” of the updates are scheduled to go dwell Thursday.
As for current mitigations, the report advised buyers use updates as before long as probable using procedures other than BIOSConnect. It even further advised disabling BIOSConnect and shown two procedures for performing so. Dell also released an advisory even further detailing advised mitigations and workarounds.
Alexander Culafi is a author, journalist and podcaster based in Boston.








